Industry Control Systems (ICS)
An industrial control system (ICS) is an electronic control system and associated instrumentation used for industrial process control. Control systems can range in size from a few modular panel-mounted controllers to large interconnected and interactive distributed control systems (DCSs) with many thousands of field connections. Control systems receive data from remote sensors measuring process variables (PVs), compare the collected data with desired setpoints (SPs), and derive command functions that are used to control a process through the final control elements (FCEs), such as control valves.
Larger systems are usually implemented by supervisory control and data acquisition (SCADA) systems, or DCSs, and programmable logic controllers (PLCs), though SCADA and PLC systems are scalable down to small systems with few control loops.[1] Such systems are extensively used in industries such as chemical processing, pulp and paper manufacture, power generation, oil and gas processing, and telecommunications.
Three Categories
ICS can, more or less, be categorized into one or more of these three categories:
View: watch the current state of the process in order to make decisions.
Monitor: monitors the current state of the process. It's distinguished from the view function since it also includes alarm and event conditions and warning of adverse process conditions.
Control: activate and control valves, motors and other components to actually drive changes in a physical state of machinery.
The Purdue Reference Model
The Purdue Reference Model, or just “Purdue Model” as it is now called in ICS communities, is widely used to describe the major interdependencies and interworking between all the major components in a major ICS. There are five levels:
- Process: also known as the EUC ( Equipment Under Control) level, this is where physical equipment that is being controlled by level 1 is located: drives, motors, valves, etc. This is where the actual physics of the process are manipulated.
- Basic Control: primary location for PLCs and VFDs. This level comprises the BPCS (Basic Process Control Systems), which applies to non-safety-related control systems.
- Area Supervisory Control: shares some functionalities with level 3 but also is where process cell or line-level functions exists for local control over individual areas of a process. Here actual ICSs start to appear, such as PLCs and VFDs (Variable Frequency Drives). Main systems at this level include HMIs.
- Site Manufacturing and Operations Control: while levels 5 and 4 exist solely on the IT network, levels 3 and below stand at the OT network. Typically contains SCADA's supervisory aspect, DCS view and control access/control rooms. It's the primary layer for operator-level interaction with the system for monitoring, responding to alarms, managing uptime and availability, among others.
- Site Business Planning and Logistics: IT systems used at each site, plant or facility to control operations. Takes orders from level 5 and monitors performance at lower levels. The ICS-DMZ is the secure, hardened layer for sharing information between OT and IT.
- Enterprise Zone: where the supply chain is managed. ERP systems such as SAP are used to understand and respond to supply and demand in order to manage work orders. ICSs are usually not connected to this level, but accurate and timely info is paramount for OT networks and ICS components.
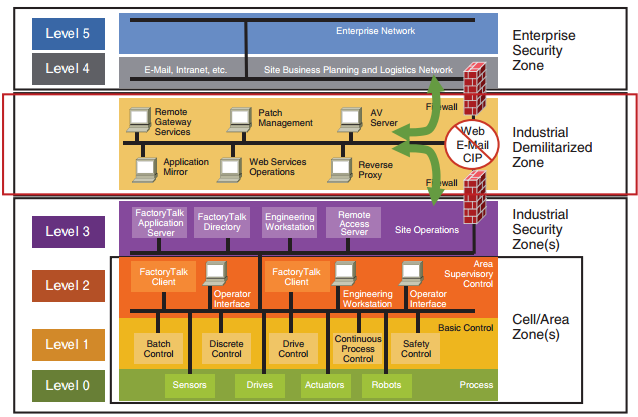
Safety Layer
All of these levels (0–5) interact to ensure the process performs its designed function. Depending on which adaptation of the Purdue Model you are referencing, you can either find the safety layer included as part of the Process Level (Level 0) or logically below the Process Level, in a manner of speaking. The safety layer is when hardware fault or other entropic adverse conditions cause a breakdown in the overall system that could result in dangerous failure. Within the safety layer are a number of what are known as engineered layers of protection. These include anything from logic coded “interlocks,” to instructions in PLCs on how to respond to adverse events, to Safety Instrumented Systems (SIS), to physical safety controls such as relief valves that ensure conditions such as too much pressure can never physically occur on a given process.
Types of Common Control Systems, Devices, and Components
-
SCADA: the Supervisory Control and Data Acquisition system mainly refers to a grouping of many ICS types in a wide geographic area. A SCADA system is all of the individual control and communication components that comprise an overall system. Examples are water utilities, gas pipelines, power transmission and distribution systems.
-
DCS: Distributed Control Systems are often large-scale systems used automate thousands of I/O points in large facilities like oil and gas refineries and chemical plants. The main difference between DCS and SCADA is that the later has been traditionally used in wider, more dispersed geographic operations, whereas a DCS in often within the four walls of a plant.
-
PLC: Programmable Logic Controllers are found in nearly every plant, these devices are widespread in plant environments but also in elevators, ramp controls, the cars we drive. They have three main components: microcontroller, expansion slots and the backplane.
-
HMI: The Human-Machine Interface is the "view" of the ICS. They may be as simple as a small panel. Most often they use a keyboard or touch-sensitive monitors that help operators manage the overall process and input commands for specific components.
-
SIS: Safety Instrumented Systems are there for when things don't go as planned. They are highly engineered, specialized control systems. They are usually designed to provide a few core funcitons, mainly to bring processes to a safe state or initiate safe system shutdowns. It's important to note that they are not widely used.
-
VFD: Variable Frequency Drives are "smart" motors. A variation of a small-scale PLC, referred to as a drive controller, that mantains a program that responds either to manual input or demand by control programs to change the speed of their attached drives.
OT Networks !== IT Networks
These OT networks (where ICSs are) are not the same than an IT network and this difference should not be taken lightly. OT systems have real life immediate implications and usually rely on a high-time availability (e.g gas, electricity, water, etc). IT networks are mostly virtual and can be rebooted, reinstalled; OTs usually take much longer since their operations are usually much more sensitive and important. That's why ICSs are mostly not connected to the internet, to minimize the attack surface area and reduce risks. Also, that's why these systems and components should not be confused with IoT, since those are devices literally connected to each other via the internet.
Want to know what a real life ICS related cyber attack looks like?
- Stuxnet worm: substantial damage to the nuclear program of Iran
- Zotob worm: knocked 13 of DaimlerChrysler’s U.S. automobile manufacturing plants offline
- Ukraine power outage
Closing
I'd like to recommend the book Hacking Exposed: Industrial Control Systems, in which this post is based on.